With PortalGuard, we offer both the ability have the users reset their password on their own. If you’d like to also configure the ability for the users to see their password instead of resetting it, that is available too. From the PortalGuard Admin Guide, which can be found here:
PortalGuard Installation and Administration Guide
Password Reset - Users can reset their forgotten passwords after sufficiently proving their identity via challenge answers, authenticating biometrically/providing OTPs sent to their mobile device or alternate email address or both.
Password Recovery - Users can recover or see their current password after sufficiently proving their identity via challenge answers, authenticating biometrically/providing OTPs sent to their mobile device or alternate email address or both.
Why do you want this feature?
If you are an old guy like myself, resetting passwords is just another necessary bane of our existence that we need to do, get right, and get them done and out of the way so we can address the next concern of life. Hopefully, this time, you remember your new password. Similar to your users, they do not want to admit they forgot their password by asking for help, and they do not want someone else fixing these issues for them. With Self-Service Password Reset (SSPR), it is simple, fast, and secure. What else can administrators ask for?
And for older administrators, they do not want to spend their time resetting the CEO's password daily. There are more crucial tasks at hand, and organizations are paying high costs for administrators, but not to expend resources on having to reset everyone's password every 30 days.
How does it work with Microsoft’s Active Directory (AD) or Azure Active Directory (Azure AD)
PortalGuard supports multiple user repository types for network credentials including AD and Azure AD. With the SSPR feature, the user’s changed password is propagated to the user repository: you reset the password once in within the PortalGuard browser and it “syncs” the password with user repository.
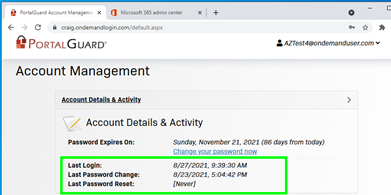
For example, here is a PortalGuard instance that has a “hybrid” connection to both AD and Azure AD with a user AZTest4@ondemanduser.com that we will reset.
Before reset:
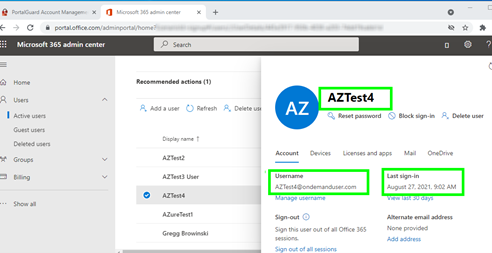
Here is the user in Azure-AD:
Also, here is the user attributes displayed by using PowerShell commands:
PS C:\WINDOWS\system32> Connect-MsolService
PS C:\WINDOWS\system32> Get-MsolUser -EnabledFilter EnabledOnly -SearchString "AZTest4" | select DisplayName,LastPasswordChangeTimeStamp, SignInName, whencreated
DisplayName LastPasswordChangeTimestamp SignInName WhenCreated
----------- --------------------------- ---------- -----------
AZTest4 8/23/2021 8:47:49 PM AZTest4@ondemanduser.com 11/23/2020 8:37:47 PM
This user has been configured so that they can reset their own password within PortalGuard:
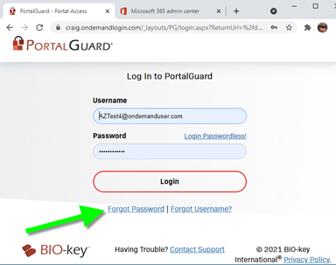
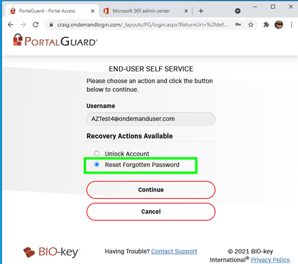
In this case, the user has been configured to answer a previously defined question:
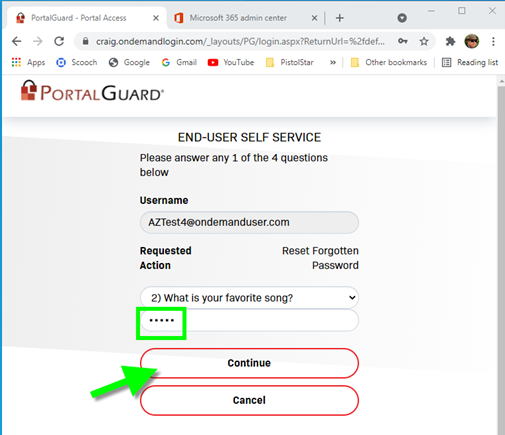
Also, the user has defined a Two Factor Authentication (2FA) when resetting their password. In this case, we are using Authy Push, but other 2FA methods are available:
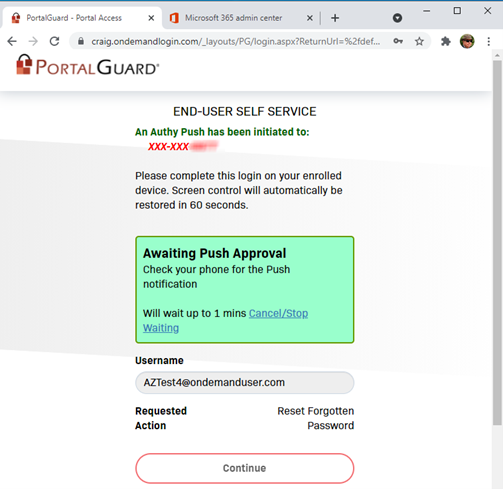
Once the Authy Push is approved from the user’s cell phone, the user is directed to reset their password, with the password rules that have been defined by the administrators:
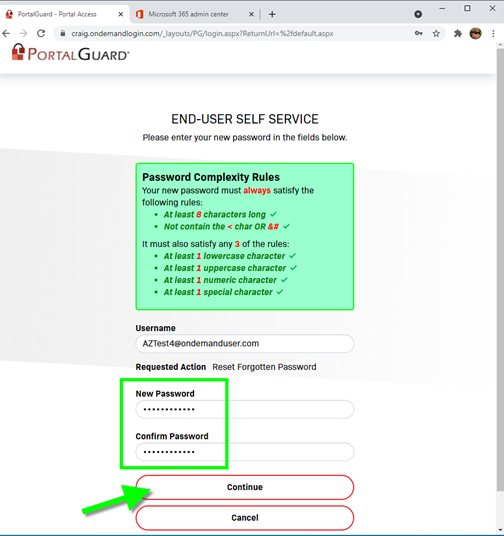
The user will show a message confirming their password reset:
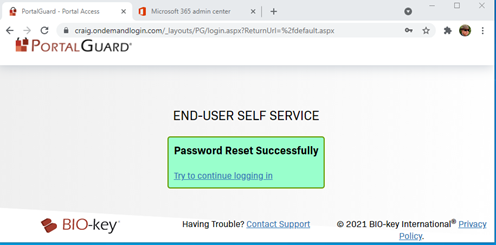
Once logged in, the user can see their Password Reset activity:
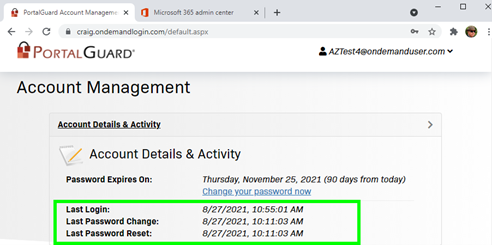
How Administrators See Reporting and User Insight
The administrators can also see the Password Reset activity in MULTIPLE places:
PS C:\WINDOWS\system32> Get-MsolUser -EnabledFilter EnabledOnly -SearchString "AZTest4" | select DisplayName,LastPasswordChangeTimeStamp, SignInName, whencreated, StsRefreshTokensValidFrom
DisplayName : AZTest4
LastPasswordChangeTimestamp : 8/27/2021 2:11:03 PM
SignInName : AZTest4@ondemanduser.com
WhenCreated : 11/23/2020 8:37:47 PM
StsRefreshTokensValidFrom : 8/27/2021 2:11:03 PM
Also, from the PortalGuard Administrative Panel:
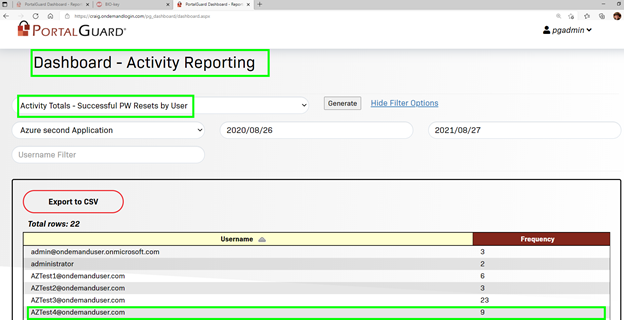
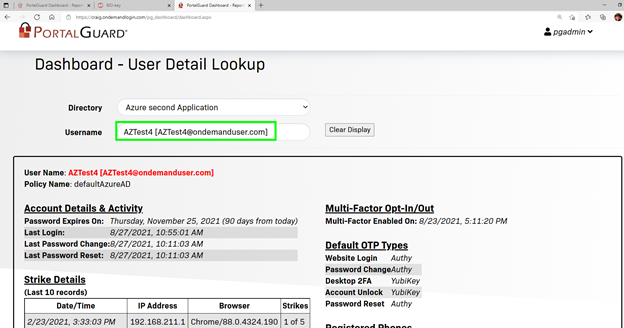
From the User Detail Lookup screen in the Administrator Dashboard:
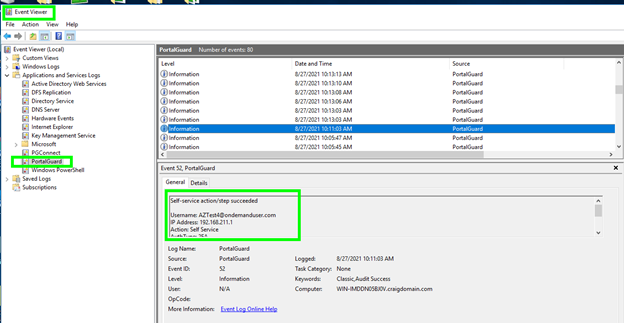
Also, on the PortalGuard server, the administrators can check the Event Viewer to see the Password Reset activity:
Active Directory (AD)
Active Directory Password Reset functionality works the same way as Azure-AD. The user experience does NOT change regardless of repository type.
Here is an example of an AD user resetting their password:
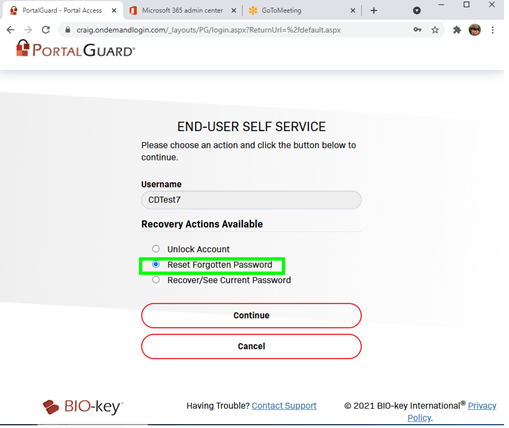
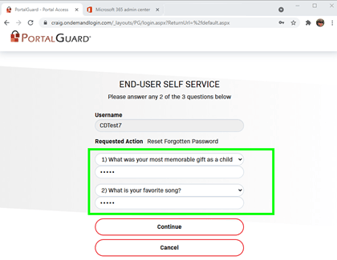
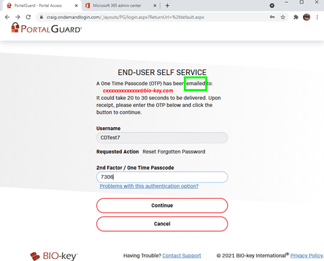
The reset methodology can be configured for different user group security policies. This user must answer two security questions and have an email passcode entered to reset the password:
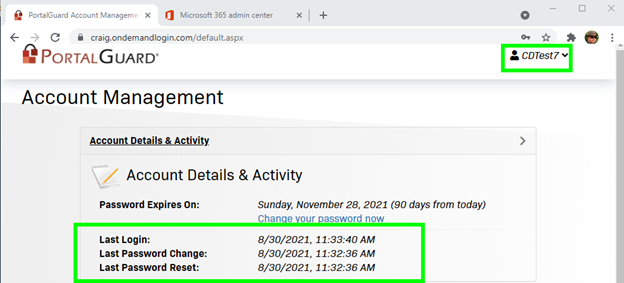
The user’s profile has been updated with the last password change and last password reset:
Active Directory properties displays the password changed date, which is the same date and time in the Account Management page above: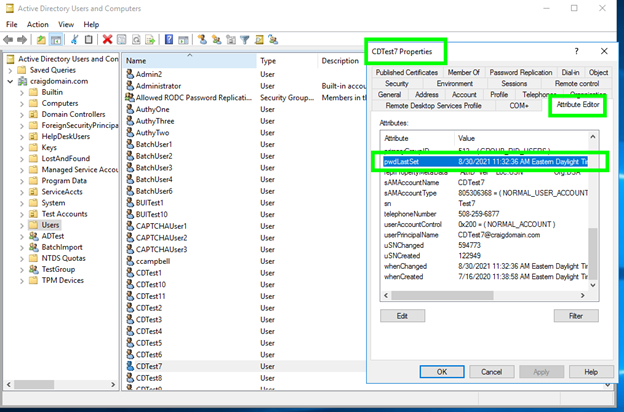
Choosing a Multi-Factor Delivery Method for Password Recovery
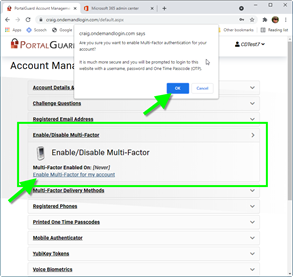
Your administrator may have allowed you to Enable Multi-Factor authentication and choose which method to use when resetting your password.
From the Account Management page, select Enable/Disable Multi Factor:
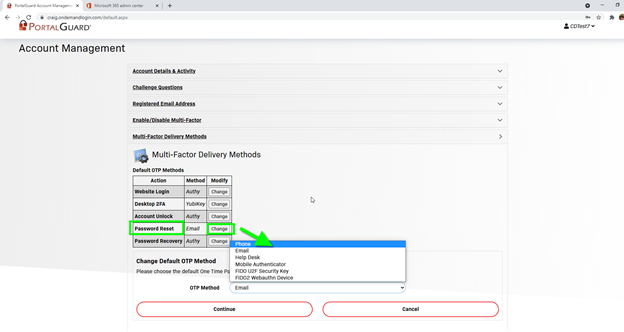
Then, select the Multi-Factor Delivery Methods for Password Reset. Choose which method you prefer to receive your OTP from the drop-down box and press the Continue button:
How Admins Setup with PortalGuard Configuration Editor
If you are an administrator using PortalGuard, this section will assist with Password Reset functionality.
Run the PortalGuard Configuration Editor on your PortalGuard server. There may already be several Security Policies associated with different user groups. Edit or Create a policy that that you choose to configure Password Reset:
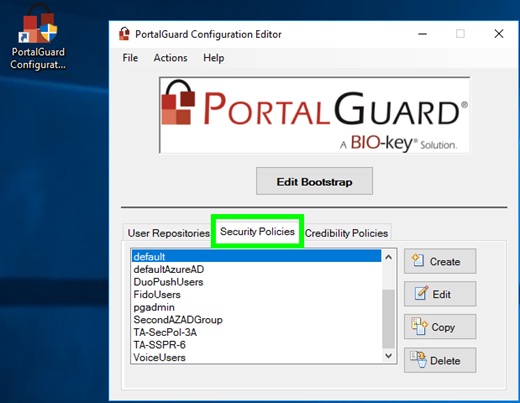
Select Actions → PW Reset → Authentication
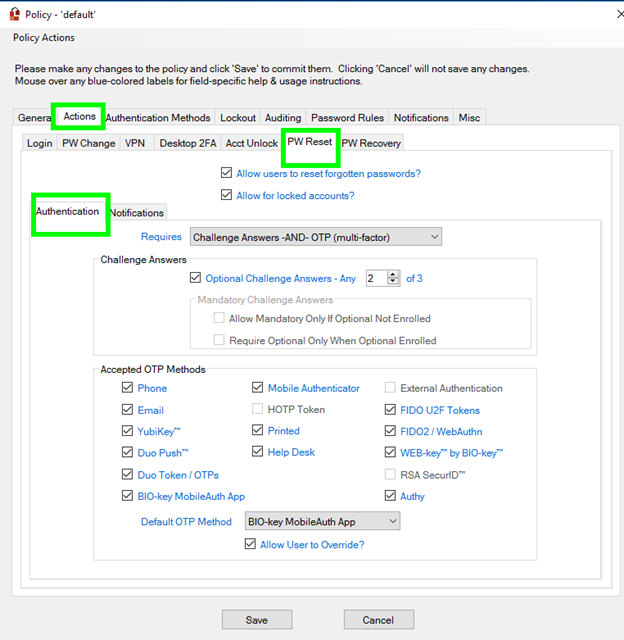
On this screen, you can:
- Define if the user can have single or multiple combined authentications
- The number of Challenge Answers if any
- They Accepted OTP method that have been previously configured
- The Default OTP Method
- Allow the users to Override the OTP method
Select Actions → PW Reset → Notifications
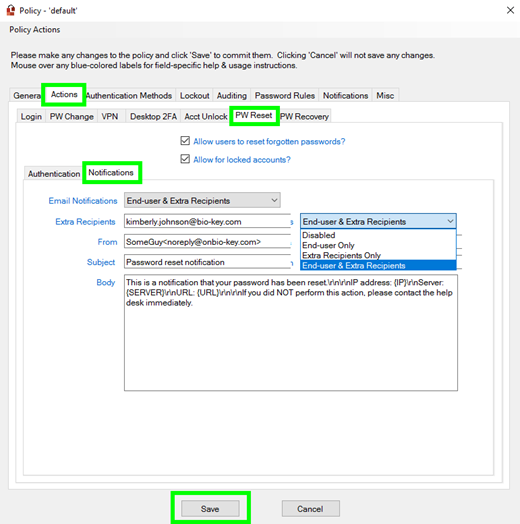
On this screen, you can:
- Define if notifications are sent went a user resets their password
- Who receives the notification
- The subject and body of the notification
Choose PortalGuard for SSPR
For IT administrators, supporting an entire user base can be taxing for IT departments, and with password resets costing $75 per incident, self-service password reset has never been more necessary than before.
With PortalGuard, IT administrators can setup the Password Reset functionality easily. This makes it easy and simple for users including the CEO's to reset their passwords by themselves. PortalGuard's SSPR solution provides users with password reset and recovery, account unlock, end-user self registration, and forgotten username lookup. Administrators can also utilize MFA and SSO in addition to the SSPR capabilities, allowing for organizations to have a secure yet user-friendly experience.
Try PortalGuard's SSPR for yourself with our free trial sandbox demo. Click here to try it out!