
Over 85% of the world’s population own a smartphone in 20231, and many smartphone vendors, such as Samsung and Apple, have introduced biometric authentication capabilities to enhance the overall user experience, including fingerprint scanning, face, and voice recognition. In fact, Cisco reported that 81% of all smartphones have built-in biometrics capabilities in 20222.
As more users adopt smartphone-based biometric authentication to log in to their mobile devices and access applications, the question of privacy and security inevitably comes up.
In this blog, we will explore biometric authentication in mobile phones, including how it works, key use cases, and the risks and benefits of using smartphone biometric authentication for enterprises.
What is Biometric Authentication on Smartphones?
Biometric authentication on smartphones measures the physical or behavioral characteristics of a user (such as fingerprints, palmprints, face, iris, retina, and voice) to determine and verify their identity before granting access to the device, application, or online account. This type of authentication can be used in place of the traditional password method, or as part of the multi-factor authentication (MFA) process, especially when accessing personal confidential data.
Biometric authentication has rapidly gained popularity in recent years and is now the default method for many smartphone users because of its convenience and ease of use. Not coincidentally, many people regard biometrics as a reliable authentication method3.
What are the Use Cases for Smartphone Biometric Authentication?
Growing demand for safe, secure, and convenient authentication from both consumers and enterprises is expected to boost the global mobile biometrics industry, which is projected to reach an overall market valuation of around US$ 208 billion by 2032.
For many organizations today, smartphone biometric authentication is used as a form of passwordless authentication to access corporate applications. In a passwordless MFA process, when an employee attempts to log in to a web application, the employee is prompted to enter their name and password (knowledge factor). A notification is then sent to the authorized user’s registered smartphone asking them to perform biometric authentication on the device (possession factor). This ensures that the employee in possession of the registered smartphone at the time of the login request is in fact the authorized user. If authentication is successful, the employee is granted access to the web application.
Aside from passwordless authentication, smartphone biometrics is also used across various industries to improve the convenience of existing processes and workflows.
Travel and Hospitality
Select airlines and airports are offering passengers the option to enter airline lounges and pass through TSA using smartphone biometrics. In these scenarios, travelers enroll their biometrics in advance via their smartphone, the system then links their biometrics to their travel documents. Then at each checkpoint at the airport, they simply present their biometrics which are matched to their travel documents to verify their identity. Other airport processes, such as check-in, bag-drop, and boarding can also be completed with smartphone biometrics to create a seamless journey for travelers. Similarly, hotels and hospitality companies are integrating mobile biometric authentication into their identity verification processes to enable seamless and secure check-in and check-out, and access to guest services and amenities like the pool and gym4.
Financial Services
The adoption of smartphone biometric authentication in financial services has taken off compared to other industries.
One of the scenarios that most people are familiar with is the biometric authentication process when logging in to a mobile banking app5. Based on the user’s predefined authentication method, the app may ask the person to scan their fingerprint or perform a facial recognition scan to verify they are the rightful owner of the device. Smartphone biometric authentication may completely replace passwords, passcodes, and knowledge-based authentication, or may be layered over traditional authentication methods to deter fraud and protect against account takeover attacks.
Smartphone biometrics also offers an easy, secure way for new customers to open an account from anywhere, with their mobile device. For example, new users may be asked to take a photo of their ID and capture their biometrics using their smartphone. The system then checks that a genuine identity document matches the biometrics of the person presenting the document. Using smartphone biometric authentication to verify customer identities not only speeds up the account opening process but also reduces customer acquisition costs for organizations.
Mobile payments – like Apple Pay and PayPal – are another popular instance of using biometrics on a mobile device. Users can make payments and transfers directly from their mobile devices after verifying their identity via biometric authentication on their smartphones. However, when it comes to high-value transactions, most organizations require additional security verification.
For more information, check out our blog on how biometrics are addressing the growing cybersecurity issues in financial services.
Online Retail and e-Commerce
Smartphone biometric authentication has been gaining traction in online retail and e-commerce. Driven by growing consumer demand for secure authentication, businesses are now invested in ensuring the security of their customers’ data and transactions, and smartphone biometrics is an increasingly popular authentication method given its high availability and user adoption rates.
Online retailers are incorporating smartphone biometric authentication into the login process to strengthen data security, which is more secure and user-friendly than passwords. This includes mobile app logins, where biometric functionality is added to the app using the manufacturer's API frameworks, and browser logins, where smartphone biometric authentication is added to a website via the Web Authentication API (WebAuthn). Once implemented, businesses can prevent data breaches by verifying customer identities and ensuring that only the account owner has access to their personal information, such as contact and payment details.
With the introduction of 3D Secure 2.0, smartphone biometric authentication has become one of the standard methods for authenticating cardholders, enhancing the security of e-commerce transactions, and protecting businesses and their customers from fraud and identity theft. Authenticating with smartphone biometrics has made the online checkout experience quicker and more seamless, improving the customer experience by removing friction from the payment process. This also means that online shoppers are less likely to abandon their shopping carts, increasing business for e-commerce merchants.
Healthcare
Considering that patient misidentification is a widespread problem, biometric authentication on mobile devices allows healthcare providers and first responders in the field to quickly identify patients and retrieve their records, especially in situations where patients are unable to assert their identity and lack any form of physical identification. This ensures that medical staff have access to the correct patient data and, therefore, can expedite quality care and provide the proper treatment for the right patient. That means fewer medical errors, safer prescribing practices, increased clinical productivity, as well as a positive impact on the patient experience.
Smartphone biometric authentication is also commonly used to enable secure and convenient access to electronic health records, online healthcare services, and telemedicine portals. For example, Northwell Health is enabling smartphone biometric authentication for users to sign in to their Northwell Health mobile app account6, where they can easily schedule and manage appointments, as well as pay bills, find doctors, access medical records, and get directions.
How does Biometric Authentication on Smartphones work?
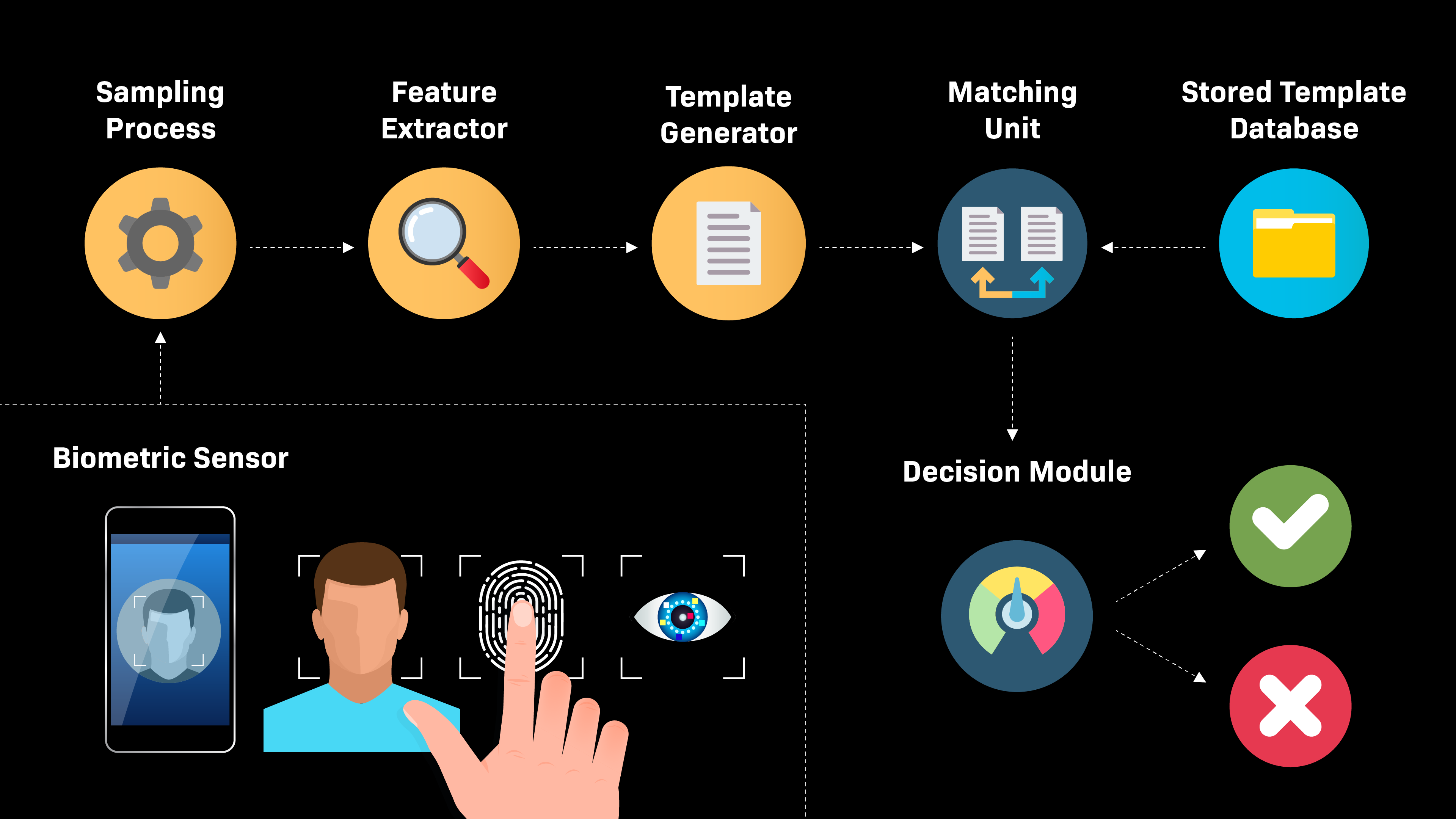
The smartphone biometric authentication system works by comparing the biometric template of the previously enrolled user with the biometric template generated at each login attempt.
A mobile biometric authentication system consists of the following units:
- An input sensor that captures a user’s biometric information. Most smartphones are now equipped with advanced sensors, including touch screens, cameras, fingerprint scanners, and microphones to collect users’ biometric data.
- A process that samples the captured biometric information to determine if the quality is good enough to be used in the authentication process.
- If the quality is poor, the person may be asked to capture their biometrics again
- If the quality is acceptable, the unique features are extracted, analyzed, and converted into a mathematical file, known as a biometric template.
- A database where the user’s biometric templates are stored and retrieved for the authentication process. Template data can be encrypted once it enters the database. Most smartphones equipped with biometric capabilities store biometric data locally on the device, as opposed to an external cloud-based server.
- A matching unit that performs a one-to-one comparison of the newly acquired biometric template with the user’s biometric template stored in the database.
How Reliable Is Biometric Authentication on Smartphones?
When it comes to biometrics, 100% matches are impossible. Instead, smartphone biometric authentication systems compare the biometric templates and generate a type of “risk score” for the login attempt. This score determines the likelihood that the person requesting access is the same as the one who initially registered on the smartphone. If the risk score is within a set threshold, access is granted; if not, access is denied.
In other words, the reliability of biometric authentication in smartphones is greatly influenced by the system’s thresholds:
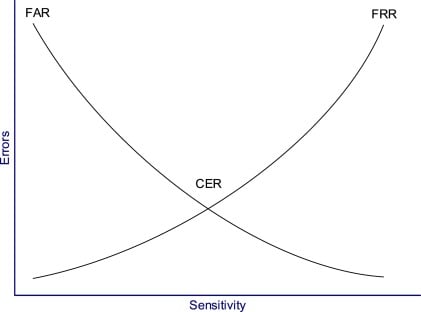
- The stricter the thresholds are, the more secure and accurate the system will be. However, this may increase the likelihood of users being falsely denied access to their own devices or accounts, thus yielding a higher false rejection rate (FRR).
- The more lenient the thresholds are, the less secure and accurate the system will be. Potentially, this may increase the chance of an imposter being falsely authenticated via biometric spoofing, thus yielding a higher false acceptance rate (FAR).
The crossover error rate (CER) or equal error rate (EER) describes the overall accuracy of a biometric authentication system and is the point where the FRR and FAR are equal.
As the sensitivity of a biometric system increases, FRRs will rise and FARs will drop. Conversely, as the sensitivity is lowered, FRRs will drop and FARs will rise (see diagram below).
What are the Benefits and Risks of Using Smartphone Biometric Authentication?
Organizations that are looking to adopt or currently supporting biometric authentication on mobile devices should consider the balance between the associated costs and benefits.
Benefits of Using Smartphone Biometric Authentication
The biggest advantage of using smartphone biometric authentication is the degree to which biometrics enhance levels of convenience and assurance in authentication.
Using smartphone biometrics for authentication is very convenient and highly accessible — no special hardware is required. Users only need to present their biometrics by placing their finger on the smartphone scanner or looking at the device's camera, faster than typing out a complex password that has multiple special characters. Users also do not need to remember anything to complete the authentication process, nor do they need to reset or refresh their biometric factor like for passwords when they are lost or forgotten. Smartphone biometrics makes the authentication process easier and quicker, which means improved productivity for employees and cost savings for the IT team when it comes to user support and management.
Smartphone biometric authentication is also more secure than knowledge-based authentication (e.g., passwords and security questions) because biometrics cannot be stolen or compromised. Biometric authentication on mobile devices verifies tangible, real-world traits, including something the user has (smartphone) and something the user is (biometrics). Each person's biometrics are unique, meaning that smartphone biometrics are only ever linked to a single individual, thus providing a high degree of certainty that the individual logging in is indeed the owner of that device or the authorized user of an application.
Risks of Using Smartphone Biometric Authentication
As with any authentication method, smartphone biometric authentication also has its risks. Some of the risks you should consider are as follows:
- Device-centric architecture
With smartphone biometric authentication, the users’ data is stored on the device and never transmitted across networks or collected on centralized servers. Today's smartphones also take important measures to protect the biometric data on the device, such as advanced encryption and isolation techniques, but that does not guarantee users’ data will remain secure forever.
Hackers are continuously looking for ways to penetrate biometric defenses and smartphone biometric authentication can be bypassed if a hacker gains control of the user’s device. This is especially the case when biometric authentication in smartphones is misconfigured, which can expose the user’s device and online accounts to then execute takeover attacks.
- Fallback mechanism
Unfortunately, biometric authentication does not completely replace passwords in smartphones. If a biometric authentication attempt fails, the device will rely on the user’s PIN or password as the fallback mechanism to unlock the device. This means that if a user chooses a weak password, a hacker can easily access the device by bypassing the biometric authentication process and forcing the device to fall back to a password.
- Biometric spoofing
Biometrics are unique but they can still be spoofed. Biometric spoofing refers to any scheme by which a fraudster defeats biometric data validation and impersonates another individual.
While extremely time-consuming to pull off, biometric spoofing in smartphones has been proven to be successful on multiple occasions:
- A Vietnamese security firm cracked Apple's FaceID in iPhone X with a composite mask made from 3-D-printed plastic, silicone, makeup, and simple paper cutouts.
- A German computing club tricked Apple's TouchID in iPhone 5S using a fingerprint mask made from latex milk and breathed on for moisture.
- The same German computing club also defeated the iris-recognition feature in Samsung's Galaxy S8 smartphone using a printed artificial eye and contact lens.
Considering this, smartphone biometric authentication is not foolproof. Malicious actors can spoof biometric authentication using various techniques and such attacks are known as presentation attacks.
However, the complexity that comes with attempting to steal and replicate biometric data makes it extremely unlikely for hackers to attempt. In addition, improved anti-spoofing models and liveness detection capabilities have been added to smartphone biometric authentication systems to prevent digital identity fraud.
- Performance issues
False acceptances happen when the smartphone biometric authentication mechanism falsely recognizes an unknown individual and grants access, especially if the individual is spoofing biometrics. The expected false acceptance rate for biometric authentication on mobile devices today is less than one in a thousand. For example, Apple reports the probability that a random person could unlock your iPhone or iPad is 1 in 50,000 using Touch ID and 1 in 1,000,000 using Face ID. Nonetheless, manufacturer-published performance metrics are usually based on optimal testing conditions, which may not be true or achievable in real-world conditions.
False rejections, on the other hand, occur when the rightful user is not recognized and is falsely denied access to their devices. False rejections can cause frustration for authorized users, decreased productivity due to poor access conditions, and increased expenditure of resources to revalidate authorized users. To combat false rejections, organizations should enable alternative modes of access via multi-factor authentication, so that genuine users are granted access even if their biometric data is not recognized.
- Legal challenges
Biometric data is classified as personally identifying information and is subject to regulations such as BIPA and GDPR, whereby violations and non-compliance can result in fines and legal actions.
- User adoption
Even as biometric authentication becomes more standard on mobile devices, and smartphone penetration increases further, a portion of your user population may choose to bypass the smartphone biometric authentication process, harming a company's overall security posture.
Likewise, some users may be reluctant to trust smartphones with their biometric data, which can create a tricky situation for organizations looking to do a full-scale implementation of smartphone biometric authentication.
Moving to a Server-Centric Architecture with Identity-Bound Biometrics
Biometric authentication via smartphones does offer organizations an easy way to authenticate users into corporate applications and accounts, but good enough is never good enough when it comes to protecting and securing access to your data.
For organizations looking to maintain a passwordless experience while addressing the security risks associated with mobile biometric authentication systems, we recommend moving to a server-centric architecture with BIO-key's Identity-Bound Biometrics (IBB).
IBB verifies the user’s identity, rather than credentials or a device, and therefore is not affected by the fallback mechanism, presentation attacks, and device hacking. Moreover, IBB enables control and oversight of the enrollment process, which prevents unauthorized delegations. Also, unlike the device-centric architecture in smartphone biometric authentication, IBB only requires users to enroll once to set up access across multiple devices and locations
The authentication methods supported by IBB are outlined below:
- For users who prefer authenticating with a smartphone: BIO-key MobileAuth
BIO-key MobileAuth is the only multi-factor authentication app that brings the power of IBB to any mobile device with palm scanning and facial recognition capabilities. Pairing MobileAuth with BIO-key's Identity and Access Management solution: PortalGuard enables users to securely authenticate into any system, desktop, workstation, and application. Read more about MobileAuth
- For users who do not want to authenticate with a smartphone, or are not permitted to use a smartphone in the workplace: BIO-key Fingerprint Scanners
BIO-key offers a variety of Microsoft-qualified Windows Hello USB scanners that can be used out of the box with Windows Hello and Windows Hello for Business, or for use with BIO-key's PortalGuard solution to secure access to desktops, workstations, and applications.
Key Takeaway
Organizations that support and manage smartphones should be aware of the security risks associated with the device-centric architecture of smartphone biometric authentication systems. Organizations looking to implement passwordless authentication should consider moving to a server-centric architecture with BIO-key's Identity-Bound Biometrics solutions to create a secure and seamless authentication experience for users across devices and locations.
Interested in learning more? Download the Identity-Bound Biometrics data sheet or get in touch with our expert team today.
Sources:
- How many smartphones are in the world? | Bank My Cell
- Cisco report: 81 percent of all smartphones have biometrics enabled | Biometric Update
- Online Authentication Barometer | FIDO Alliance
- How Biometrics Helps Modernize the Hotel Guest Experience | Hotel Technology News
- Ways to Secure Mobile Payments on Apps | Fifth Third Bank
- Mobile app: What is a Face or Touch ID? | Northwell Health