Are you and your IT team utilizing the best cybersecurity practices? Maybe you are, but the rest of your company doesn’t even know the basics.
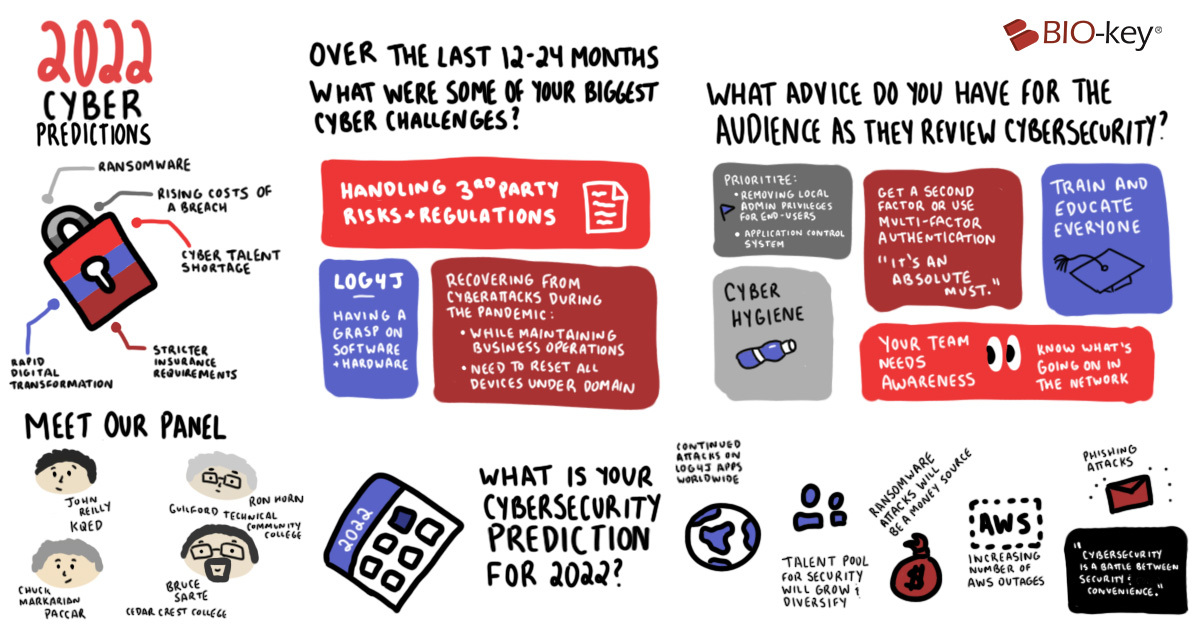
During our 2022 Cyber Predictions webinar, we asked our panel of CISOs from a wide range of industries, “What advice do you have for companies reviewing their cybersecurity?”. Surprisingly enough, our panel all had very similar advice. From improving cyber hygiene to prioritizing education for your staff and executives, the advice they shared was some they wished they had before they undergone cyberattacks.
What does our panel advise for companies reviewing their cybersecurity strategies? What major changes do IT teams need to make in 2022? Are there new solutions you should know now? Read more and find out.
“People push for convenience. Cybersecurity is the ongoing tension between security and convenience, right? Including myself, I pushed for convenience. I think that’s our fatal flaw, so social engineering in some ways will get hackers the keys to the kingdom faster than any other method. I predict we’ll see a rising awareness of social engineering and how hard it is to spot.”
John Reilly, Executive Director of IT and Enterprise Systems, KQED
What should you do from a technology standpoint?
If you haven’t done this already, do it first.
One, remove local administrator privileges for end-users. Your end-users do not need administrative access to perform their job, and in most cases, just need cloud access and a laptop. Allowing your users to have local admin privileges increases the risk of an insider attack succeeding or a cyberattack compromising more data.
If you have the budget and the IT staff to support this, you should implement Microsoft’s LAPS (Local Admin Password Solution) which manages local passwords. When your users log in locally, there is an increased risk of the Pass the Hash credential replay attack. With LAPS, it changes the password to a different, random one at intervals.
Two, implement an application control system. An application control system can flag any unknown or forbidden executables that try to run on any machine. For organizations that have Windows and Active Directory, having an application control system can prevent ransomware executables.
Multi-factor Authentication, you ABSOLUTELY need it.
Your company like many others allows for some amount of remote access into your systems, and if this is true, you NEED multi-factor authentication or some sort of second factor. If you don’t already have MFA, talk to your executives or leadership team to get it implemented.
Stay clean and be cyber hygienic.
Like washing your hands and practicing basic hygiene, getting your users to practice cyber hygiene is a must. There are some simple yet effective steps your users can take, like frequently updating passwords and being aware of phishing attempts. More importantly, however, is patching and updating your systems. If something's been patched for, a vulnerability can't take advantage of it.
“If you only allow me one thing I could do in security, is we would be the absolute best patching because that'll take away probably 95% of your real risk. So just those would be my two things is MFA and patching general hygiene.”
Chuck Markarian, Chief Information Security Officer, PACCAR
How do you get your users involved?
Start training and educating everyone today.
From an administrative perspective, training everyone like faculty, employees, peers, and your leadership team is crucial to improving cybersecurity measures. It’s a tough ask to get everyone involved, especially when you haven’t been hit with a cyberattack, so many see it as a waste of time, but education is the best way to mitigate the risk.
If you clearly explain the gravity of a cyberattack and articulate the steps needed to implement a defense, you'll instill confidence in your leadership team and illustrate that there is a tangible ROI on IT investments. After all, more funding and resources only come if your team knows the landscape, how to navigate it and where the path forward leads.
The last step of the journey to a secure network may seem rudimentary, but its value cannot be overstated: awareness. When you and your team know what’s happening both inside and outside of the network, the appropriate structures and responsibilities can be put in place across the organization. In turn, critical information can be shared seamlessly amongst all team members to better prevent potential attacks before they happen.
Now, what's next?
With cyberattacks occurring more frequently than ever before, everyone must be aware of cybersecurity basics and equipped to practice fundamental cyber hygiene. As a whole, an organization's security is only as strong as its weakest link - so even if you're not part of the IT team, we all have a shared responsibility.
This advice comes from our 2022 Cyber Predictions webinar, but it's just the tip of the iceberg. Watch the full webinar to get insight on:
- Our CISO panel's predictions for cybersecurity activity throughout 2022
- Unique solutions to major issues they faced in the past 12 to 24 months
- The unforeseen effect of recent cyberattacks on cyber insurance claims