"Russia Hammers Ukraine with Massive Cyber-Attack". While you would assume this is a "hot headline" blasting across the media in response to the Russian invasion of Ukraine this week, this is actually a headline from a Business Insider article published in 2014 - 8 years ago. The Russian cyberattack history on Ukraine is much longer (and dedicated Wikipedia page) than many people think. The Ukraine cyber attacks in 2014 and throughout the years since have continued to have a major impact, felt not only in the country, itself, but also around the globe.
With this week's invasion and the cyber events leading up to it, cybersecurity professionals are again on high alert. Cyberattacks and the malicious software used to conduct them do not see geography as a boundary to be respected. When a cyberattack is conducted in Ukraine, it is felt around the world.
A Long History of Attacks
One of the most memorable moments of my career was in October 2018. I was sitting in an audience full of security and risk professionals at a BitSight customer event, as the former head of the Ukraine Computer Emergency Response Team (CERT) took the stage. He proceeded to describe what it was like to defend his country from the onslaught of cyberattacks happening during the 2014 Russian invasion of Crimea and those that followed for years after.
Former Head of Ukraine CERT speaks at a 2018 BitSight event.
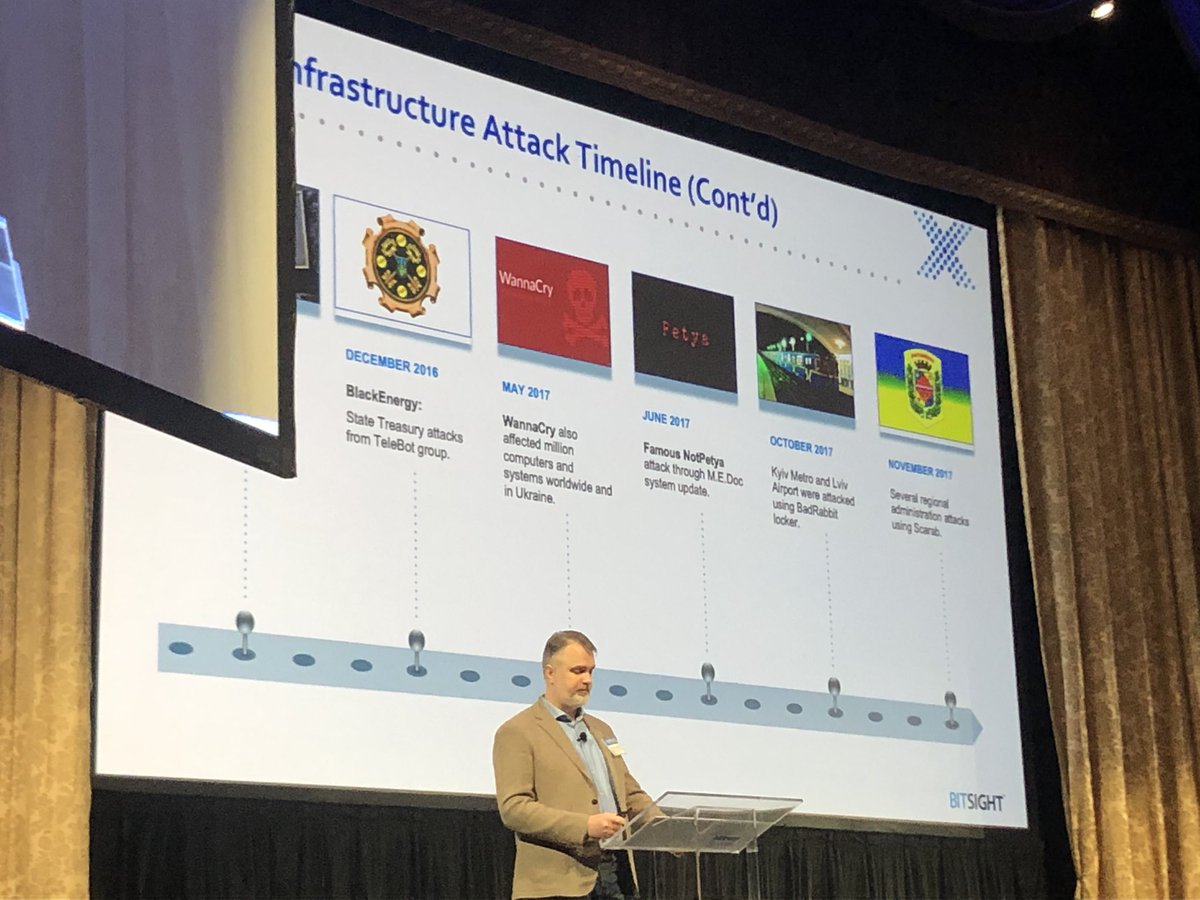
The first records of cyber warfare between these two nations date to 2005 with the release of the cyberweapon Uroburos, and attacks continuing to escalate from 2013 to 2017. The Ukraine power grid was targeted by hackers on Christmas in 2015 causing blackouts. In 2016 their State Treasury was paralyzed in December just as taxes were due from their citizens. The worst was yet to come, with one of the most infamous attacks taking place in 2017.
The Petya malware, and most famously the NotPetya variant of it, showed us just how much of a global impact this type of warfare can have. While Russia has not claimed ownership over this destructive malware and was mildly affected by it, the perfect timing of its release on the eve of the Ukrainian holiday, Constitution Day, leads experts to believe otherwise. While the target seemed to be Ukraine, the NotPetya cyber attack cost global organizations more than $10 billion and affected companies around the world, including large portions of the European Union and the United States.
The Ukraine invasion that just took place and the perfectly timed cyberattacks in the weeks leading up to the invasion are yet another event on the long timeline of this cyberwar that has been waging for years.
Recent Cyberattacks & Invasion is a Global Concern
Multiple articles came out recently, including from the Associated Press and Reuters, highlighting the waves of cyberattacks that have been part of the invasion.
Researchers reported that the malware used in attacks this week was 3 months in the making. Widespread Distributed-Denial-of-Service (DDoS) attacks happening the day before the invasion were specifically targeting Ukraine's government websites and affiliated government agencies and organizations to cause confusion before the invasion.
For weeks cyber professionals and organizations have been on high alert. For example, the U.S Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA) issued two alerts, one on January 11th, highlighting the risks from Russian-state-sponsored cyber threats. The National Credit Union Association (NCUA), along with the FBI and CISA also encouraged credit unions and their cybersecurity teams nationwide to be on alert and conduct proactive threat hunting.
CISA has also just announced their "Shields Up" alert highlighting that "every organization - large and small - must be prepared to respond to disruptive cyber activity".
With how connected we all are on a global level, building up cyber defenses and being aware of a potential cyber threat is the responsibility of all organizations - of all sizes.
What should you do about it?
Hearing how cyber attacks were able to systematically take down Ukraine's critical infrastructure, power grid, transportation, treasury, and even interfered with the Ukrainian government election should be an eye-opener. Just last year the USA got a taste of what that type of cyberattack would feel like as we felt the effects of the Colonial Pipeline attack which took down the fuel supply to a large portion of states on the east coast. This is just one attack - imagine if there were many happening at the same time.
So, what can you do about it and how can you help protect your organization and the nation from the impact of cyberattacks? Here are a few suggestions:
- Conduct a Risk Assessment - understand your level of cyber risk, how susceptible you are to cyberattacks, and where are your most critical assets need to be protected.
- Continuously Monitor Your Third Parties - the saying is that "you are only as secure as your weakest link" when it comes to the supply chain. With most organizations outsourcing parts of their business to a network of third parties or suppliers, it is critical to know who you are connected to. Going beyond a basic onboarding questionnaire and continuously monitoring the cybersecurity posture of your third parties is key to preventing attacks from coming in through those connections.
- Make Sure You Have MFA on Every Single Account - first on the list of recommendations as part of CISA's "Shields Up" alert to reduce the likelihood of a cyber intrusion is to "Validate that all remote access to the organization's network and privileged or administrative access requires multi-factor authentication." Multi-factor authentication (MFA) is known to block upwards of 90% of ransomware and other credential-based attacks. At this point you should have MFA implemented, and now is the time to make sure it is covering all access for not only your employees but your customers and suppliers as well. With many traditional MFA methods, such as SMS-based One Time Passcodes (OTPs) being hacked, an MFA strategy must include strong authentication methods, especially identity-bound biometrics so that you have ways to verify the person is who they say they are - not just their device.
- Work Towards a Zero Trust Architecture - at this point "trust no one" is becoming the best motto to follow as any implicit trust introduces a certain level of cyber risk. Consider implementing a Zero Trust architecture that uses a wide range of techniques such as granular security policies, continuous authentication, and single sign-on to make sure all access is verified before it is granted.
- Consider Geofencing - many organizations are using geofencing to establish a technological barrier as to where data can be sent to and collected from, as while as to where users are allowed to access organizational systems from. This is often applied to network traffic and authentication strategies to either completely block requests outside of the "fence" or at least require additional authentication.
A Different Type of Warfare
While the attacks are happening in Ukraine this week, as we’ve become more connected by technology and the Internet because of global digital transformation, this has continued to open avenues for these attacks to proliferate quickly.
At the same time, the method of warfare is different — and that should be acknowledged. This type of destructive attack is easily conducted, require no travel, no shipping of military troops and equipment, are low cost, and difficult to trace, in comparison with traditional military approaches. This truly is cyber warfare that challenges all cyber operations and threatens all organizations.
If you are looking to bolster your organization's cybersecurity and reduce the likelihood of a damaging cyber intrusion, visit our pages on MFA: https://www.bio-key.com/multi-factor-authentication/