
In today’s day and age, your organization is likely facing new cyberthreats, pushed to working remotely due to the COVID-19 pandemic, wanting to safeguard more sensitive files throughout the organization, or a mix of all the situations. IT administrators and managers have the difficult task of changing the cyber infrastructure to solve all these issues without heavily frustrating their users.
Organizations then look to deploying a zero-trust architecture for several reasons, including mitigating cyberthreats, increasing the efficacy of their cybersecurity protections, and safeguarding more sensitive data no matter where it lives. However, deploying zero-trust is not a simple task, and for a first-time deployment, IT admins may not know where to start. Here is where we come to help. We surveyed IT professionals from various enterprises in different verticals about zero-trust deployment. This is how they responded on zero-trust: their scope, priorities, cadence, and budget.
Scope
The scope highlights where organizations deploy zero-trust. Is there a focus on one-key department or business unit or do organizations deploy zero-trust throughout the whole enterprise? When organizations first plan zero-trust deployment, 65% of them had planned to deploy zero-trust throughout their entire enterprise. The remaining 35% only planned to limit their scope to specific business units and departments only with some not even considering zero-trust architecture. With this in mind, we know organizations are not viewing zero-trust as an “all-or-nothing" approach. Unfortunately, we had hoped more organizations planned to deploy across their whole enterprise because safeguarding less than 100% of the enterprise with zero-trust is not a strong cybersecurity strategy. When enterprises do not protect the entire enterprise, they are still susceptible to cyberthreats, and it is inevitable that safeguarded business units or departments are breached. An unsecured department can be the gateway a cybercriminal needs to access even the most heavily guarded department.
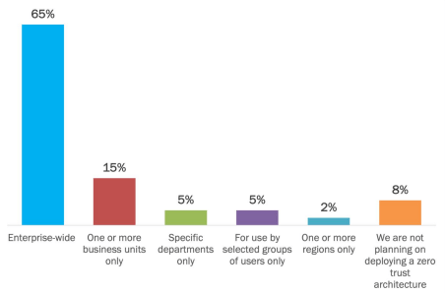
On the bright side, we do expect to see organizations that initially are planning to deploy zero-trust on one department or business unit to move to a full enterprise-wide deployment as they gain expertise and gain the initial benefits. Additionally, as aforementioned, while there are some enterprises that are not looking to deploy zero-trust, this is likely to change into next year as many organizations will allocate a budget for zero-trust initiatives over the next two years.
Priorities
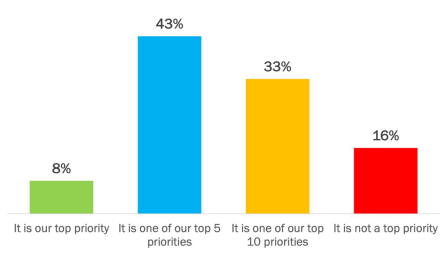
Zero-trust has become a larger trend this year because implementing a zero-trust architecture is one of the top five security priorities for most organizations. There are four main driving elements that the majority of enterprises share in deploying a zero-trust architecture: mitigating current trends and threats, achieving higher cybersecurity efficacy, strengthening protections, and safeguarding data sources. These drivers highlight the benefits of a stronger security and showcase the risks of cyber threats. Because of these drivers, many enterprises expect beneficial outcomes coming from zero trust initiatives.
However, these are not the only reasons we have seen enterprises prioritize zero-trust. Other cybersecurity initiatives compliment zero-trust approaches, like protecting sensitive data, preventing data exfiltration, and assessing the cybersecurity threat across organizations with subsidiaries. With a heightened focus on solving these initiatives, companies are turning to zero-trust architectures as a solution.
Cadence
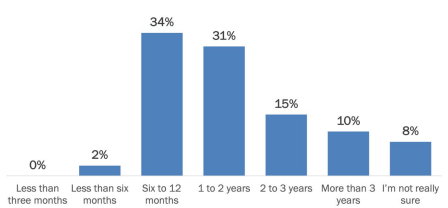
With zero-trust becoming so nuance, a lot of organizations are unsure how long zero-trust will take to deploy. The uncertainty of a how long deployment will take mixed with the decisions surrounding scope and budget factor in the confusion of how long it will take to deploy. Additionally, user adoption or lack thereof play a major role in how our respondents reacted to an expect timeframe. Two out of three organizations expect to achieve full deployment of zero-trust across the entire organization to range from three months to two years while 8% are completely unsure of how long it will take.
Oddly enough, larger organizations are expected to deployed faster than smaller ones. For example, 46% of organizations between 1,001 and 10,000 employees expect to achieve full deployment within a year while 31% of organizations with less than 1,000 employees are expected to achieve this. In fact, smaller organizations are more unsure of how long deployment will take.
Larger organizations are expected to achieve full deployment faster for several reasons. For one, they have more full-time IT staff, allowing for better resources to deploy and enable the new technology. Additionally, larger organizations have a higher urgency to deploy due to potential reputational and financial damage. The risk of these damages and other financial penalties is more significant to large organizations compared to smaller ones. There is a greater sense of urgency to mitigate the risks and utilize the best technical and organizational approaches against cybersecurity threats. The timeline might change for all organizations though as the next 12 months are critical for zero trust initiatives. Organizations will want to start reaping the early benefits now, and early successes in reducing data breaches, insider threats, and ransomware attacks will fast forward the process for remaining zero trust deployments.
Budget
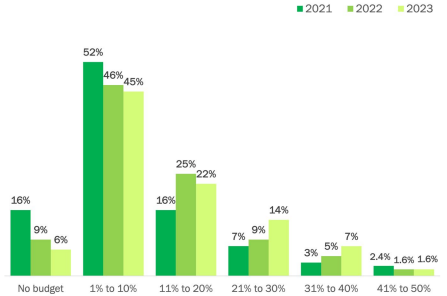
Year over year, organizations are allocating more of their IT budget to zero-trust initiatives, from having no budget in 2020 and 2021 to at least 1% to 10% in the next year. As time goes on, that allocation will increase to 11% to 20% and go up from there.
What’s Stopping Organizations Now?
Unfortunately, implementing zero-trust is easier said than done. Zero-trust initiatives can be delayed, undermined, or even stopped entirely due to major barriers. For example, dealing with limitations in legacy systems, obtaining appropriate IT sources, and rethinking how to approach security are the top three barriers for organizations to embrace zero trust. After all, it is still too early for many organizations to reap the benefits of zero-trust, but the technical and resource barriers are critically important in the initial stages of deploying zero-trust.
Legacy systems also present limitations as organizations must use general policies or redevelop the legacy systems to support zero trust. Migrating to modern systems is an option too, but that is a hefty lift and can disturb the organization for a long time. Overall, rethinking security is a major barrier for everyone in the organization. Zero trust removes the concept of separating inside the organization and outside the organization. Instead, every user now is assigned their own set of criteria that must be weighed each time they are requesting a resource. This new mindset requires a whole set of new solutions, but understanding these solutions is key to a stronger security approach.
How do IT Professionals Respond to Zero-Trust?
The Why Zero Trust is Important whitepaper explores how organizations are deploying or planning to deploy a zero-trust architecture and recommends best practices and solutions to support the move to zero-trust.
