The traditional method of authenticating to a network or endpoint uses a single factor – a combination of a username and password that the user enters to gain access. That approach is fraught with security problems, including the fact that users will generally use simple passwords that are easy for them to remember (and easy for bad actors to guess or determine through brute force techniques), they will re-use the same password on multiple systems (so that if a bad actor breaches one system he or she will be able to breach multiple systems to which that user has access), and many will write down usernames and passwords on a sticky note or in some other conspicuous place (making them easy for passersby to access).
The obvious answer to addressing the problem of single-factor authentication is to use a second factor to make access to critical network and data assets more difficult for bad actors to achieve. Two-factor authentication – or, more accurately, multi-factor authentication (MFA) – generally provides much more secure access than is possible with single-factor authentication and, if done right, without increasing the difficulty with which valid users can gain access to needed resources.
Why is MFA more secure?
The reason why MFA is much more secure than single-factor authentication is a simple one: let’s say there is a 10% chance that a bad actor will be able to gain access to any single factor used in accessing a system, resulting in a 10% chance of unauthorized access. But there is only a 1% chance that a bad actor could gain access to both factors simultaneously (10% x 10% = 1%), increasing security by an order of magnitude.
While many employees are not required to use MFA to access their corporate network or PC, it’s a commonly used concept by just about everyone. For example, when accessing an ATM, users are required to insert a card (the first factor) into the machine, followed by entering a PIN (the second factor). MFA is also widely used in various other access scenarios, such as airport security, which uses three factors (a boarding pass, personal identification and the passenger’s face) to enable access into the secure area of a terminal.
In a corporate setting, the first factor is normally a username and password combination. However, the second factor can be a number of different things, such as:
- A hardware token that is plugged into the PC, laptop or mobile device.
- A one-time password delivered to a mobile phone.
- A one-time password delivered via email.
- A mobile authenticator that generates a multi-digit code on a mobile device that the user is required to enter into the system interface.
- A soft/push token that delivers a push notification to the user’s mobile device, asking for him or her to accept or reject it.
- Biometrics, such as a user’s fingerprint, facial scan, iris scan or palmprint.
So, if MFA provides such a high level of security, why is it not employed more widely? For example, Microsoft estimates that only 18% of Office 365 users employ MFA when accessing the platform. Part of the reason is that many IT and security decision makers consider MFA too expensive or too disruptive for users, and so they live with lower security as a trade-off for avoiding the expense and perceived difficulty of implementing MFA.
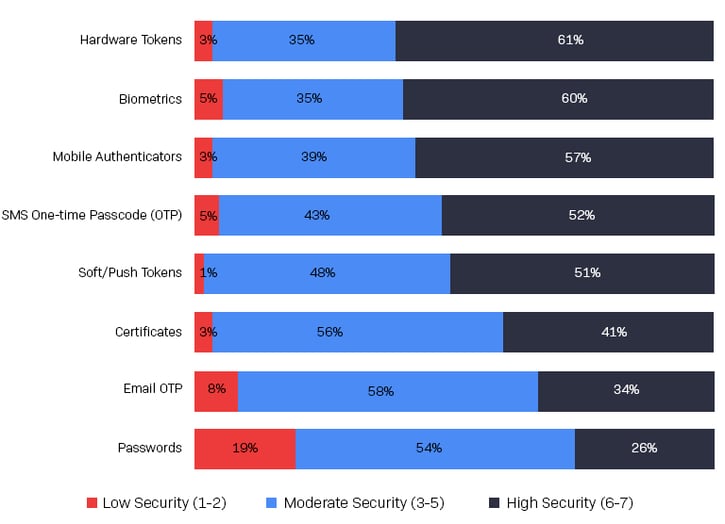
Choosing the “right” MFA solution is dependent on a number of factors: its level of security, ease of use, integration with existing workflows, cost and how it enables other initiatives across the organization. For example, although usernames/passwords are the most commonly used authentication method, an Osterman Research survey conducted in May 2021 revealed that they are viewed as the least secure access method: only 26% of IT and security team members view them as providing a high or very high level of security. By contrast, hardware tokens and biometrics are viewed as providing a high or very high level of security by 61% and 60%, respectively.
Using Biometrics with MFA
Biometrics offers a number of advantages in the context of MFA, not least of which is the fact that the second factor is always available to the user seeking access to a system. The wide range of biometric options (e.g., a fingerprint, palmprint, face, voice or iris scan) gives IT and security teams various options for touch-based and touchless access, making it easier to implement across a wide range of use cases (e.g., employees, contractors or customers). Plus, most users and customers are already at least somewhat familiar with the notion of biometrics through things like Apple Face ID on more recent iPhones or Apple Touch ID on older iPhones.
While MFA may not be as widely used as it should be, the future looks promising. The survey noted above found that 63% of organizations surveyed will increase their level of MFA spending over the next five years and 35% will keep spending at current levels. Moreover, MFA is a key element of many Zero Trust initiatives, which will spur increased use of more secure access technologies, including MFA.
In short, the use of MFA – and the much higher security it affords – will mean more secure access and, ideally, fewer security problems.
Understanding the State of MFA
With multi-factor authentication being more common in many environments, more organizations are looking to implement MFA into their own environments to mitigate security risks. However, implementing MFA is easier said than done, and many organizations may have a hard time finding a solution that works for them. Therefore, we have developed an in-depth MFA survey that determines how organizations manage security, authentication, and see decision makers' attitudes toward various authentication methods including Zero Trust, passwordless approaches, and biometrics.
Learn more about how multi-factor authentication approaches differ from more traditional methods in our State of MFA eBook.
