Josef Stalin is supposed to have once said, “I trust no one, not even myself”. While murderous dictators are normally not reliable sources of useful information, this quote properly summarizes the essence of the Zero Trust architecture, which the National Institute of Standards and Technology (NIST) defines as:
“The term for an evolving set of cybersecurity paradigms that move defenses from static, network- based perimeters to focus on users, assets, and resources. Zero trust assumes there is no implicit trust granted to assets or user accounts based solely on their physical or network location or based on asset ownership. Authentication and authorization (both subject and device) are discrete functions performed before a session to an enterprise resource is established.” [1]
What is Zero Trust?
In essence, Zero Trust is what its name implies: no user, device, asset or resource is implicitly trusted, but instead must be authenticated and approved each time it attempts to access a network, cloud service, data repository or some other resource.
So why the need for and interest in Zero Trust? In short, it’s because the network perimeter that was more or less defensible when everything was behind a corporate firewall just doesn’t exist anymore. Yes, there are still corporate assets maintained on-premises behind firewalls, gateways and the like, and this will continue to be the case indefinitely. But in most organizations, users, assets and other resources are located well outside of any defensible perimeter and are using a large number of different networks, devices, applications, and cloud services. While the network perimeter has been diminishing for some time, the COVID pandemic, ensuing lockdowns, and the rapid increase in employees working from home in early 2020 more or less made the network perimeter a relic of the past.
In support of that assertion is data from Netskope’s February 2021 Cloud and Threat Report[2]:
- In organizations of between 500 and 2,000 employees, an average of 690 different cloud apps are in use, 97% of which are considered “shadow IT” apps.
- The majority (53%) of secure web gateway traffic is now consumed by interactions with cloud services and apps.
- Nearly one-half (47.5%) of enterprise use of cloud apps is classified as “Poor”, meaning they are not safe for use in corporate applications.
- The percentage of malware that was sent through cloud apps went from 48% of all malware in 2019 to 61% in 2020.
In a nutshell, this data strongly suggests that cloud apps are exploding in popularity, particularly with employees who are working from home, the vast majority are not trustworthy, and bad actors are using them to distribute malicious content.
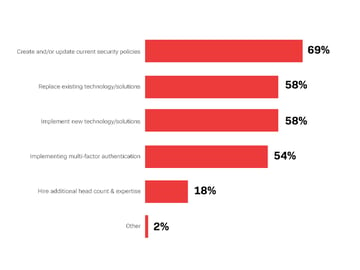
This message has not been lost on IT and security decision makers. We discovered in a survey that Osterman Research conducted for BIO-Key International in May 2021 that while only 33% of the mid-sized and large organizations have today implemented a Zero Trust architecture, another 59% are planning to do so. Among the most immediate changes these organizations have made or will make in support of Zero Trust are creating and/or updating current security policies (cited by 69% of survey respondents), replacing existing technology and solutions (58%), implementing new technologies and solutions (58%), and implementing multi-factor authentication (MFA) (54%).
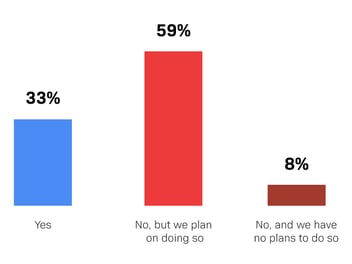
As implied by the data on Zero Trust adoption, a small percentage (8%) of organizations have no plans to implement Zero Trust. Why? In most cases, it’s not based on the perceived lack of benefits afforded by Zero Trust, but instead is simply because of a lack of time, budget or staff members to implement and manage it. Some who are not planning to implement Zero Trust are unsure of what it actually is or how to implement it, indicating that more education on its benefits will be required.
So what exactly are the benefits of Zero Trust?
- One of the chief benefits of Zero Trust is that by never trusting anyone or anything and requiring their bona fides each time they try to access the network, there is greater visibility into the identity of those attempting access, their location, when they’re accessing it, what they’re accessing, and so forth. This visibility is essential to the proper application of security and compliance policies, and it ensures that bad actors – and the data breaches they might attempt – are identified more quickly than would otherwise be possible.
- Another benefit is that the use of MFA – a key element of Zero Trust – enables more secure, and when implemented correctly, convenient access for employees and others attempting to gain access to the network.
- Zero Trust is an important element in supporting remote employees, an issue that has been front-and-center for most IT and security decision makers during the past 16+ months. Zero Trust supports remote employees by enabling their authentication to the growing number of cloud applications without undue effort by IT and security teams, thereby making remote employees more efficient and imposing less burden on IT and security.
- Finally, the use of Zero Trust is useful in preventing successful intrusion by bad actors who might use targeted phishing emails, install keyloggers on individual PCs, or move laterally through corporate networks. Because Zero Trust starts from a position of not trusting anything that happens on the network, bad actors will hit multiple and significant barriers in their attempts to use these attack techniques.
While Zero Trust is not a panacea that will prevent every network intrusion or data breach, it goes a long way toward addressing many of the key security issues that organizations face, particularly in an environment in which their attack surface has expanded dramatically.
Enabling Zero Trust through Multi-factor Authentication
To get the most use out of implementing Zero Trust, your organization needs to have a multi-factor authentication solution. MFA requires end users to provide two or more verification factors and is an added layer of security on top of a simple password. Based on the survey exploring Zero Trust in organizations, 59% are planning on doing so, and the first step to approaching Zero Trust is through implementing Multi-factor Authentication.
Learn more about how multi-factor authentication approaches differ from more traditional methods and enable Zero Trust in our State of MFA eBook.
[1] https://www.nist.gov/publications/zero-trust-architecture
[2] Source: Netskope
